16bc0adf C37d 4e53 9fb3 2ad0afd019ad 11zon Pakwheels Blog

B2dfde66 80f9 4e3d 98d9 F1ef107d7f09 11zon Pakwheels Blog You'll be starting windows install from a basically brand new, clean ssd. windows default is zero remote access, get it up and running first, before plugging the internet back in. only after. Right click fmrs.exe and then click run as administrator. the script will begin to run.

16bc0adf C37d 4e53 9fb3 2ad0afd019ad 11zon Pakwheels Blog Correlation ids are used as a starting point reference to obtain the complete error details from uls logs during troubleshooting issues. usually, uls logs are located in the 15 16 hive’s logs folder. e.g: “ c:\program files\common files\microsoft shared\web server extensions\15\logs ”. This kba lists the event ids generated by windows and are helpful during investigations around rdp attacks or common malware investigations. This error code is usually associated with the control panel and it can prevent you from accessing some of the settings and features on your computer. in this blog post, we will explain what causes this error and how to fix it in a few simple steps. To gain full voting privileges, an office 365 user discovered that around 100 emails were sent apparently from him; they have some kind of malicious pdf attachment. the message headers show "received: from xxx.xxx.prod.outlook " as the initial source of the emails.

Cd3b86af 2aa9 47a0 9293 D5c2e6d1e49e 11zon Pakwheels Blog This error code is usually associated with the control panel and it can prevent you from accessing some of the settings and features on your computer. in this blog post, we will explain what causes this error and how to fix it in a few simple steps. To gain full voting privileges, an office 365 user discovered that around 100 emails were sent apparently from him; they have some kind of malicious pdf attachment. the message headers show "received: from xxx.xxx.prod.outlook " as the initial source of the emails. Good day everyone, i finally decided to search for some help on here after struggling with blue screens multiple times a day for almost half a year now. the blue screens codes i come across are: and newly "attempted execute of noexecute memory". they must be hardware related for the following reasons:. A remote code execution vulnerability exists in the way that microsoft windows codecs library handles objects in memory, aka 'microsoft windows codecs library remote code execution vulnerability'. this cve id is unique from cve 2020 1319. The following script (also attached) can find and fix all the services that do not have quotes around the executable paths. the script will need to be run from an elevated powershell console or the powershell ise. if you get an error regarding execution policy you can run the following command. $hasimagepath = $false. I've had this error for about 3 years, after asking on the official microsoft forums and other sites, i still haven't been able to fix it. i really want to fix this once and for all. mdm.

E1c886d8 7d5f 4ca0 9f25 6c34633bd2a8 11zon Pakwheels Blog Good day everyone, i finally decided to search for some help on here after struggling with blue screens multiple times a day for almost half a year now. the blue screens codes i come across are: and newly "attempted execute of noexecute memory". they must be hardware related for the following reasons:. A remote code execution vulnerability exists in the way that microsoft windows codecs library handles objects in memory, aka 'microsoft windows codecs library remote code execution vulnerability'. this cve id is unique from cve 2020 1319. The following script (also attached) can find and fix all the services that do not have quotes around the executable paths. the script will need to be run from an elevated powershell console or the powershell ise. if you get an error regarding execution policy you can run the following command. $hasimagepath = $false. I've had this error for about 3 years, after asking on the official microsoft forums and other sites, i still haven't been able to fix it. i really want to fix this once and for all. mdm.
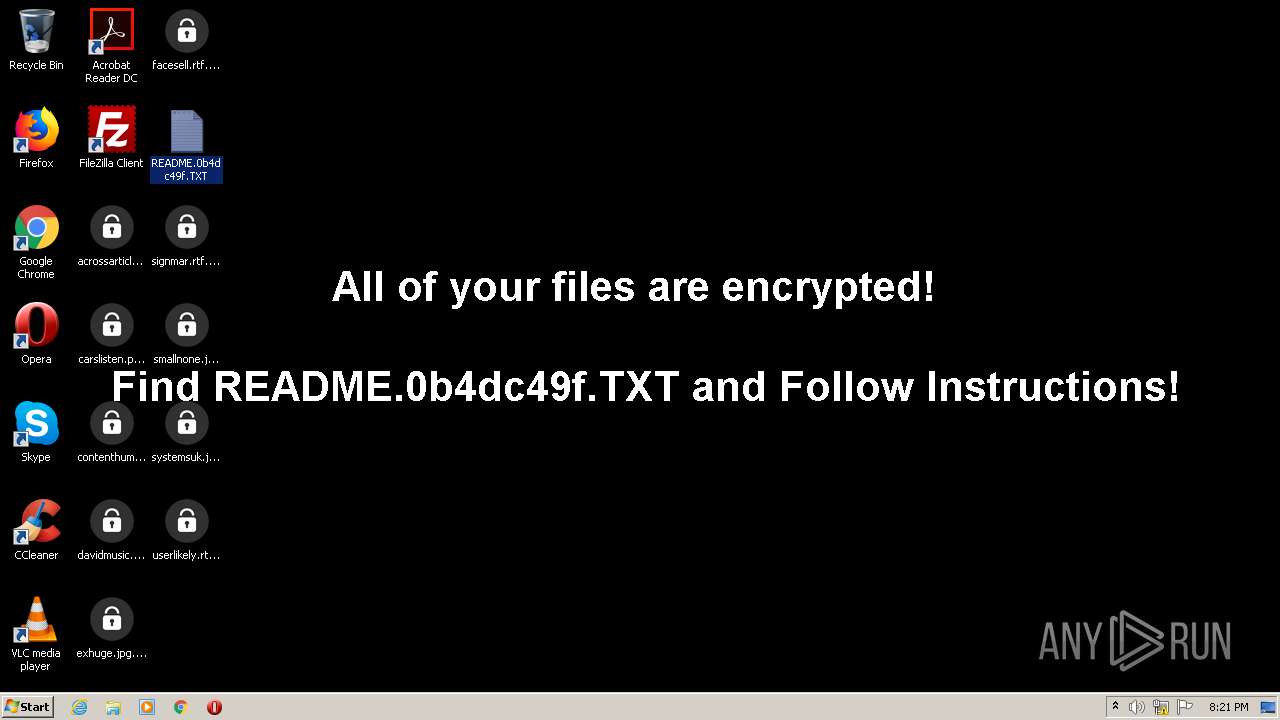
Analysis The following script (also attached) can find and fix all the services that do not have quotes around the executable paths. the script will need to be run from an elevated powershell console or the powershell ise. if you get an error regarding execution policy you can run the following command. $hasimagepath = $false. I've had this error for about 3 years, after asking on the official microsoft forums and other sites, i still haven't been able to fix it. i really want to fix this once and for all. mdm.

Comments are closed.