4 3 2 6 Packet Tracer Configuring Ipv6 Acls Answers

4 3 2 6 Packet Tracer Configuring Ipv6 Acls Ilm Pdf Configure, apply, and verify an ipv6 aclconfigure, apply, and verify a second ipv6 acl. 4.3.2.6 packet tracer configuring ipv6 acls: topology this document describes configuring ipv6 access control lists (acls) to filter traffic in a network topology.
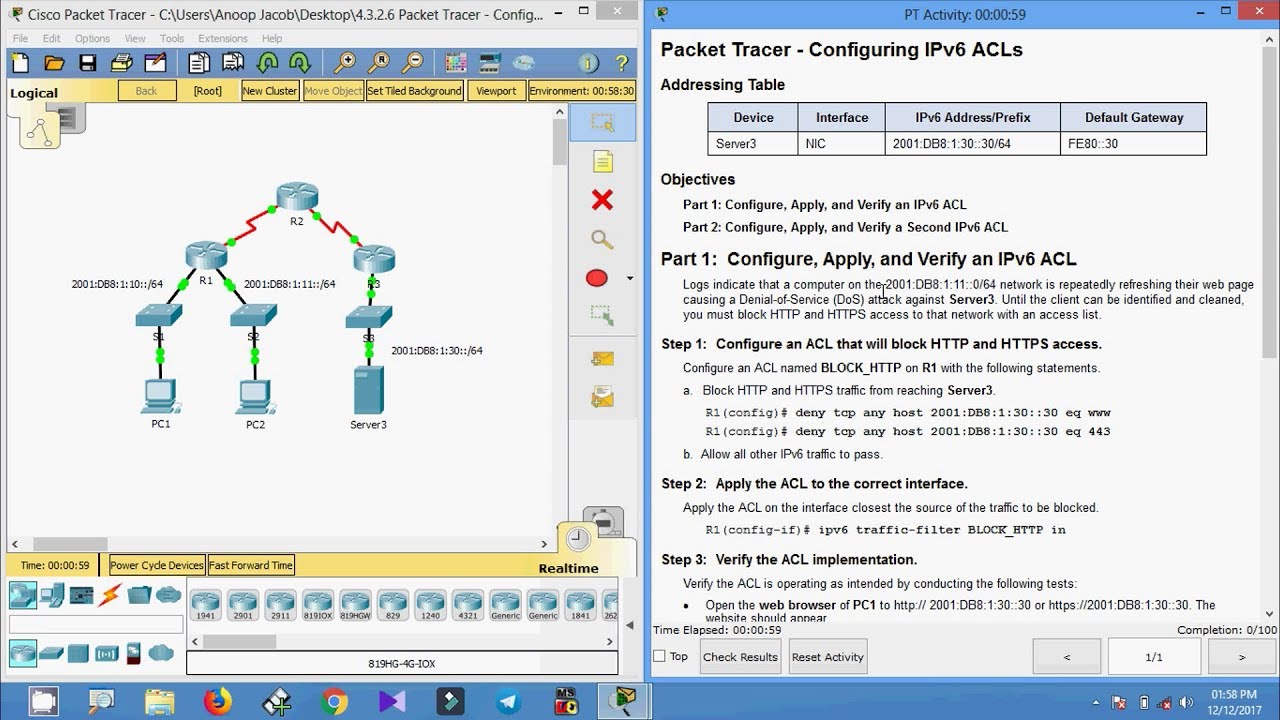
4 3 2 6 Packet Tracer Configuring Ipv6 Acls Now, let’s delve into the practical aspect of configuring ipv6 acls in cisco packet tracer. for this demonstration, we will simulate a network topology comprising a router, a switch, and multiple hosts interconnected via ipv6 enabled interfaces. This video walks through completing packet tracer assignment 4.3.2.6 configuring ipv6 acls. this packet tracer is part of the cisco r&s connecting networks. A. block http and https traffic from reaching server3. apply the acl on the interface closest to the source of the traffic to be blocked. • ping from pc2 to 2001:db8:1:30::30. the ping should be successful. a. block all icmp traffic from any hosts to any destination. Ipv6 configuration on cisco routers. in this lesson we will configure ipv6 with different ipv6 configuration styles with different examples.
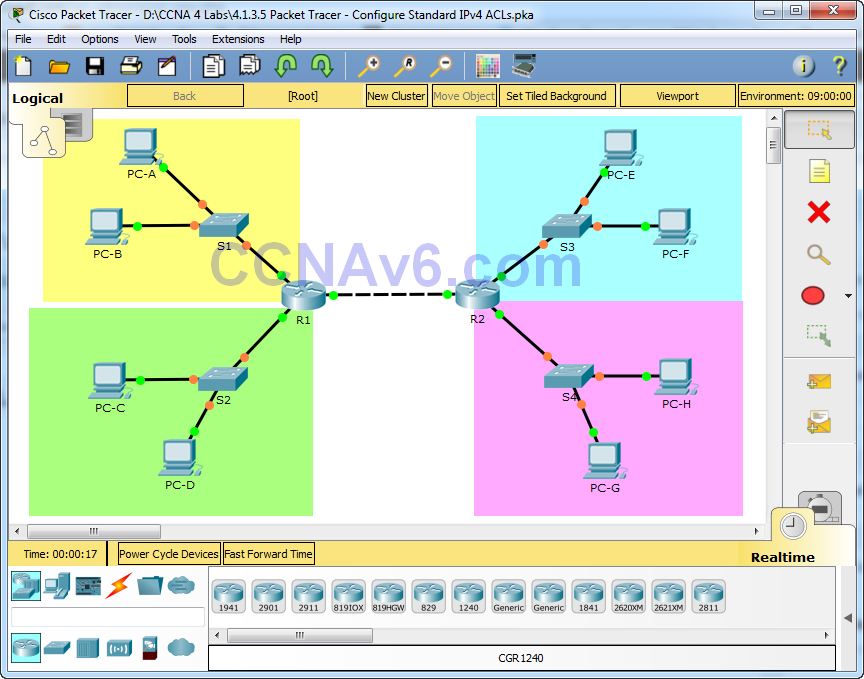
4 1 3 5 Packet Tracer Configure Standard Ipv4 Acls Answers A. block http and https traffic from reaching server3. apply the acl on the interface closest to the source of the traffic to be blocked. • ping from pc2 to 2001:db8:1:30::30. the ping should be successful. a. block all icmp traffic from any hosts to any destination. Ipv6 configuration on cisco routers. in this lesson we will configure ipv6 with different ipv6 configuration styles with different examples. Step 1: configure an acl that will block http and https access. configure an acl named block http on r1 with the following statements. block http and https traffic from reaching server3. allow all other ipv6 traffic to pass. step 2: apply the acl to the correct interface. The document describes how to configure ipv6 access control lists (acls) to block specific types of traffic. it has two parts that show how to create acls to block http https and icmp traffic respectively. the acls are applied to interfaces to filter traffic and the configurations are verified.

Comments are closed.