Example Of Deployment Scenario Download Scientific Diagram

Example Deployment Scenario | Download Scientific Diagram
Example Deployment Scenario | Download Scientific Diagram This help content & informationgeneral help center experiencesearch. Can someone please post a simple guide on making yt dlp work? question? i've read through a bunch of documentation and all i see are pages of command lines with no actual straight forward example of what you need to make this run. archived post. new comments cannot be posted and votes cannot be cast.

Deployment Diagram Template Web Based, Deployment, Getting To Know, The ...
Deployment Diagram Template Web Based, Deployment, Getting To Know, The ... Where does email sent to *@example.com go? if i accidentally sent sensitive information to *@example.com would some evil person (potentially at the iana) be able to retrieve it someday?. Hey guys! so i’m a co founder at a resume builder company (novoresume, if you’ve heard of us), and while developing the platform, i’ve looked at 1,000 resumes and analyzed what differentiates a good resume from the bad. and, well, i ended up learning a lot. i’ve been lurking on reddit for like forever and wanted to give a bit back to the community. so, i created this mega list of all. Technically example.com and www.example.com are different domain names. one could have 2 completly different websites on them (although that's quite bad practice). When a client connects to https://www.example.com, it will start with the ssl negotiation, and the user will get a warning that the ssl certificate does not match. any redirect that you create will happen only after the ssl negotiation, so they will still be getting the ssl certificate warning.

Deployment Diagram Example Templates | PPTX
Deployment Diagram Example Templates | PPTX Technically example.com and www.example.com are different domain names. one could have 2 completly different websites on them (although that's quite bad practice). When a client connects to https://www.example.com, it will start with the ssl negotiation, and the user will get a warning that the ssl certificate does not match. any redirect that you create will happen only after the ssl negotiation, so they will still be getting the ssl certificate warning. Here’s an example for my latest role. notice how i try to use as many of the same words as the job description: for now, just put down the qualifications without any regard for style. also, you don’t need qualifications for all the requirements. we’re only going to use the top two anyway. struggling to come up with qualifications?. For example, a text rule containing "a*c" would format cells with "abc," "ac," and "abbc" but not "ab" or "ca." to match a question mark or asterisk in text, you can escape the wildcard characters by adding a tilde (~) in front of them. Http: example.com paths: path: /foo(/|$)(.*) backend: servicename: echo svc serviceport: 80 in this ingress definition, any characters captured by (.*) will be assigned to the placeholder $2, which is then used as a parameter in the rewrite target annotation. this ingress will do the following: requests to /foo will be delivered to echo1. Your ldap root is dc=example,dc=com, and you use an o style tree under that. dn's could very well be, cn=bobs,ou=users,o=company,dc=example,dc=com in general, your need to be compatible with 3rd party ldap client is what should drive your structure. if it needs a dialect, it'll probably need to look as active directory like as possible.

Deployment Diagram Example Templates | PPTX
Deployment Diagram Example Templates | PPTX Here’s an example for my latest role. notice how i try to use as many of the same words as the job description: for now, just put down the qualifications without any regard for style. also, you don’t need qualifications for all the requirements. we’re only going to use the top two anyway. struggling to come up with qualifications?. For example, a text rule containing "a*c" would format cells with "abc," "ac," and "abbc" but not "ab" or "ca." to match a question mark or asterisk in text, you can escape the wildcard characters by adding a tilde (~) in front of them. Http: example.com paths: path: /foo(/|$)(.*) backend: servicename: echo svc serviceport: 80 in this ingress definition, any characters captured by (.*) will be assigned to the placeholder $2, which is then used as a parameter in the rewrite target annotation. this ingress will do the following: requests to /foo will be delivered to echo1. Your ldap root is dc=example,dc=com, and you use an o style tree under that. dn's could very well be, cn=bobs,ou=users,o=company,dc=example,dc=com in general, your need to be compatible with 3rd party ldap client is what should drive your structure. if it needs a dialect, it'll probably need to look as active directory like as possible.
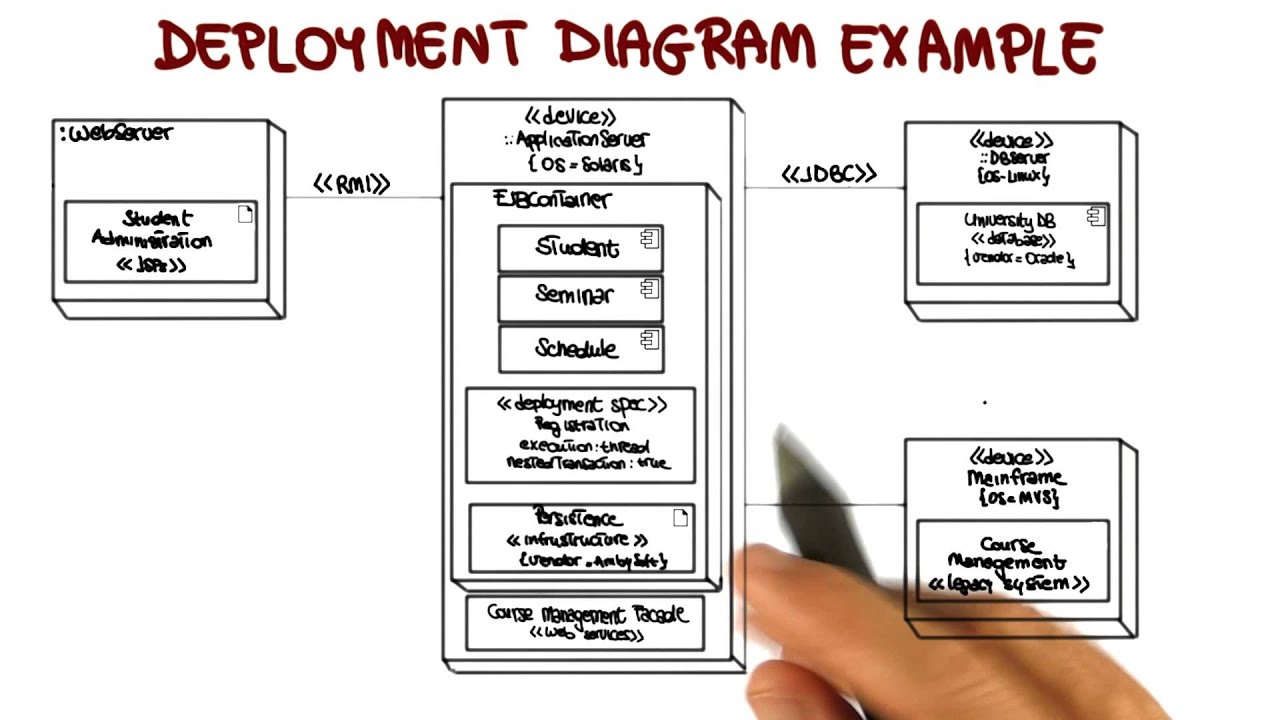
UML Structural Diagrams: Deployment - Georgia Tech - Software Development Process
UML Structural Diagrams: Deployment - Georgia Tech - Software Development Process
Related image with example of deployment scenario download scientific diagram
Related image with example of deployment scenario download scientific diagram
About "Example Of Deployment Scenario Download Scientific Diagram"

















Comments are closed.