Malware Analysis Anyrun Exe Malicious Activity Any Run Malware

Learn Malware Analysis With #ANYRUN | ANY.RUN Posted On The Topic ...
Learn Malware Analysis With #ANYRUN | ANY.RUN Posted On The Topic ... I get messages "website blocked due to port scan" these are outbound scans. these alerts pop up in the lower left corner of my desktop about 20 times a day! it's very annoying. i have run the malware bytes scan on my desktop windows 10 computer, and the scan come back clean. i tried to figure o. This is a business productivity tool used by every member of our team for unified business communication. google workspace, slack, crm, and more. the latest version of malwarebytes nuked this on all our pcs. that's a significant hit to our ability to work, and a loss of productivity as we go thro.

Malware Analysis For Keeping Up With The Latest Threats
Malware Analysis For Keeping Up With The Latest Threats Malware.ai.3578383182, c:\users\karin\appdata\roaming\bittorrent\updates\7.10.5 46075.exe, quarantined, 1000000, 716584114, 1.0.93942, 80a027848c3c9af9d549cb4e, dds, 03159004, 51a77462c1373628edd33f8d77841211, 1ae76dd5ba659c1b0567af6b91e10f6e9e700d5d61da63a81f6cb845c82a4ac6 should i worry?. I had my malwarebytes av and defender disabled when i downloaded a fishy file from an online github source. when i switched my pc back on, it was seeming to running slower, much slower than before. whenever i open taskmgr, i see a process called "system interrupts" on top using 20 30% of my cpu,. I have been recently getting a notification that a trojan was blocked called hb305v5lb.puzzletake.com via msedgewebview2.exe. i have never used microsoft edge i use firefox but i know that some of the software is used for other programs. luckily malwarebytes has been consistently blocking the con. Hello! just this evening malwarebytes detected two unwanted programs or malware files, and i went ahead and quarantined them. i have not deleted them yet, they remain in mwb quarantine. what steps should i take now to further scan and protect my system, and is there any way of knowing if any harm.

ANY.RUN - Interactive Malware Analysis Service On LinkedIn: #anyrun # ...
ANY.RUN - Interactive Malware Analysis Service On LinkedIn: #anyrun # ... I have been recently getting a notification that a trojan was blocked called hb305v5lb.puzzletake.com via msedgewebview2.exe. i have never used microsoft edge i use firefox but i know that some of the software is used for other programs. luckily malwarebytes has been consistently blocking the con. Hello! just this evening malwarebytes detected two unwanted programs or malware files, and i went ahead and quarantined them. i have not deleted them yet, they remain in mwb quarantine. what steps should i take now to further scan and protect my system, and is there any way of knowing if any harm. Https://downloads.malwarebytes.com/file/mb5 offline hi, is the official offline installer also updated or does the update only come via the update function of the. Hello. on my slowly dying windows 10 pc, i had a lifetime malwarebytes pro disc program installed on my computer, and i would like to know the instructions on how to remove it from that computer so that i can use it on a new computer. your help will be appreciated. Hello, i have malwarebytes identifying powershell.exe as malware. i'm unsure if it's a false positive? it keeps popping up every 5 min but running the threat scan both for malwayebytes and others comes out empty. i'm attaching the screenshot of the popup. my system is running on windows 11 and it. Lummastealer also known as lummac2 is a type of malicious software (often classified as an information stealer or infostealer) designed to surreptitiously collect sensitive data such as login credentials, browser cookies, cryptocurrency wallet information, and other valuable personal or system de.
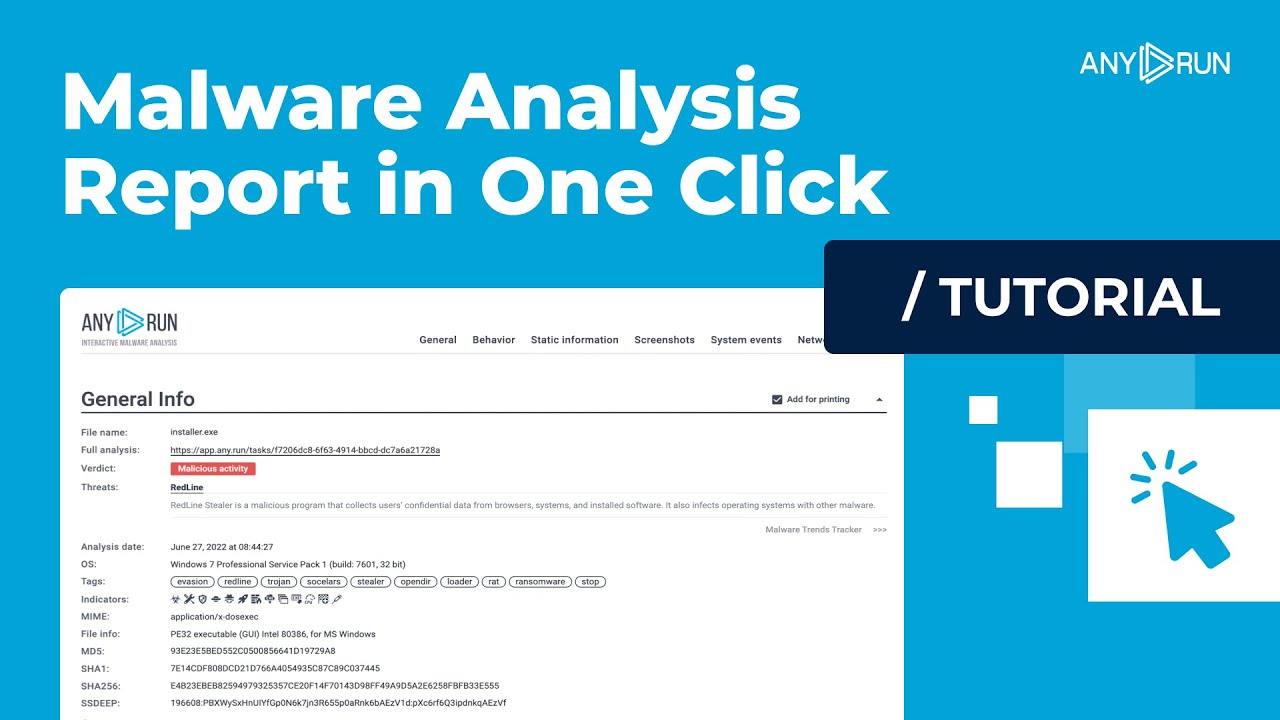
Get Malware Analysis Report in One Click – ANY.RUN Tutorial
Get Malware Analysis Report in One Click – ANY.RUN Tutorial
Related image with malware analysis anyrun exe malicious activity any run malware
Related image with malware analysis anyrun exe malicious activity any run malware
About "Malware Analysis Anyrun Exe Malicious Activity Any Run Malware"

















Comments are closed.