More Than Just Identity Access Management How To Install Ibm

Identity And Access Management System 1 0 Pdf Provisioning Ibm Notes Ibm installation manager will be used to install ibm products like ibm websphere & ibm http server (ihs). extract and install the installation manager using account which has root privileges. siva pokuri. thanks for providing this informative information you may also refer. By leveraging identity observability and identity posture management, we proactively detect and mitigate risks, ensuring least privilege access and compliance across hybrid environments.

What Is Identity And Access Management Iam Ibm Identity and access management (iam) enables you to securely authenticate users for platform services and control access to resources consistently across the ibm cloud platform. Certified iam consultants and security specialists can extend your teams to plan, design, deploy and manage outcome driven identity solutions. work together with our services professionals to maximize iam investments and set up programs for long term success. These steps provide information about installing ibm security directory server with the ibm passport advantage packages that are provided with the ibm security identity manager product. To install and configure ibm® security directory server version 6.4, which is included with verify identity access, see ibm security directory server v6.4 documentation. the instructions in the following topics are for directory server version 6.3.
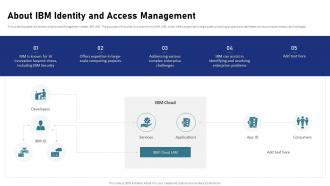
Iam Process For Effective Access About Ibm Identity And Access Management These steps provide information about installing ibm security directory server with the ibm passport advantage packages that are provided with the ibm security identity manager product. To install and configure ibm® security directory server version 6.4, which is included with verify identity access, see ibm security directory server v6.4 documentation. the instructions in the following topics are for directory server version 6.3. Ibm® quick start guide for the identity manager virtual appliance this guide gets you started with a typical installation of identity manager. national language version: to obtain the quick start guide in other languages, access the pdf files on the quick start package. Here are the steps to install ibm i access client solutions (acs): download the acs installer: go to the ibm i access client solutions download page and download the latest version of the acs installer for your operating system (windows, macos, or linux). Identity and access management is key to the secure access of your organization’s business assets, especially in today’s era of compliance. but traditional identity and access management takes a technology driven approach to protecting against security threats and vulnerabilities. Learn about how to deploy ibm verify identity access oidc provider environments.
Identity Access Management From Ibm Bankinfosecurity Ibm® quick start guide for the identity manager virtual appliance this guide gets you started with a typical installation of identity manager. national language version: to obtain the quick start guide in other languages, access the pdf files on the quick start package. Here are the steps to install ibm i access client solutions (acs): download the acs installer: go to the ibm i access client solutions download page and download the latest version of the acs installer for your operating system (windows, macos, or linux). Identity and access management is key to the secure access of your organization’s business assets, especially in today’s era of compliance. but traditional identity and access management takes a technology driven approach to protecting against security threats and vulnerabilities. Learn about how to deploy ibm verify identity access oidc provider environments.

Comments are closed.