Ssh Tunneling Summary 300 Watts
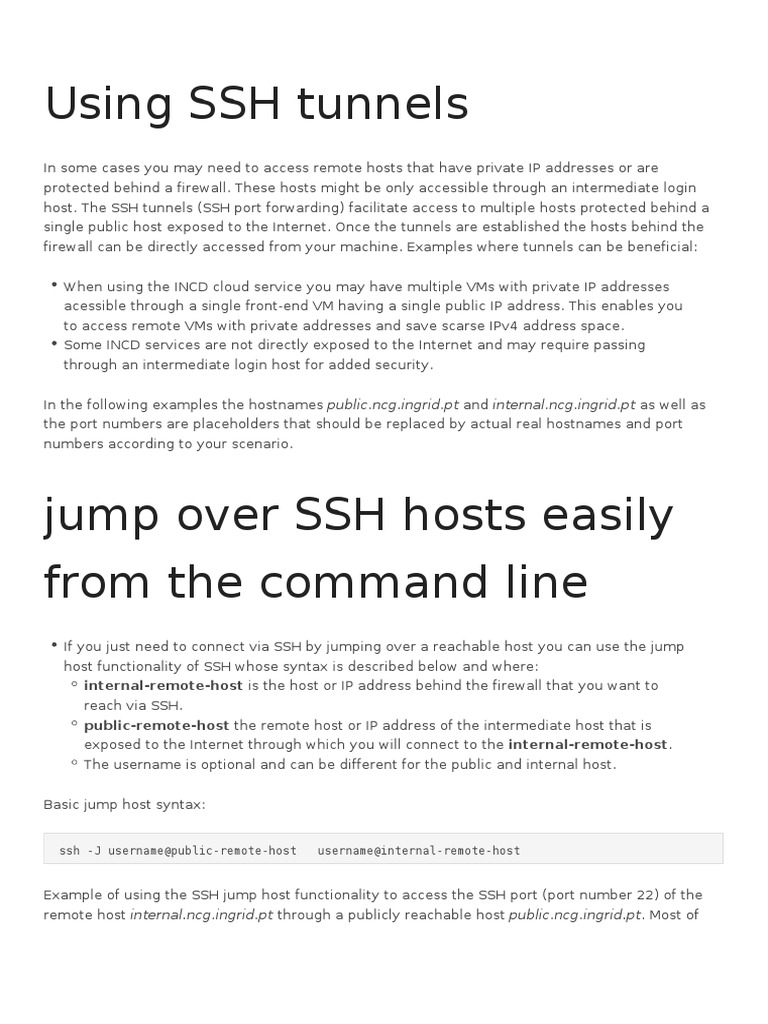
Using Ssh Tunnels Pdf Port Computer Networking Proxy Server Ssh server: a machine that can be sshed into by client; target server: a machine to which you want to establish a connection, usually to open services on this machine to the outside world. notice: both client and ssh server can be target server, it doesn’t really need three machines to perform port forwarding! however, dynamic port forwarding. Tunneling是这样一种概念:将一种网络协议报文 (这里更多指应用层协议)封装到另外一个协议中传输,这里我们就是ssh,也就是说将其他协议的报文封装到ssh中,由于ssh本身是加密的,因此所有的应用层网络通信都是加密安全的. 在ssh tunneling的技术中,我们会绑定一个local port,并且所有targeted到这个local port的报文都将透明的加密并通过隧道转发到remote system,正因为如此,ssh tunneling也被称为端口转发。 为什么需要ssh tunneling? ssh虽然对于管理远端系统是足够了,但是ssh并不足以用于访问所有远端系统所提供的服务。.
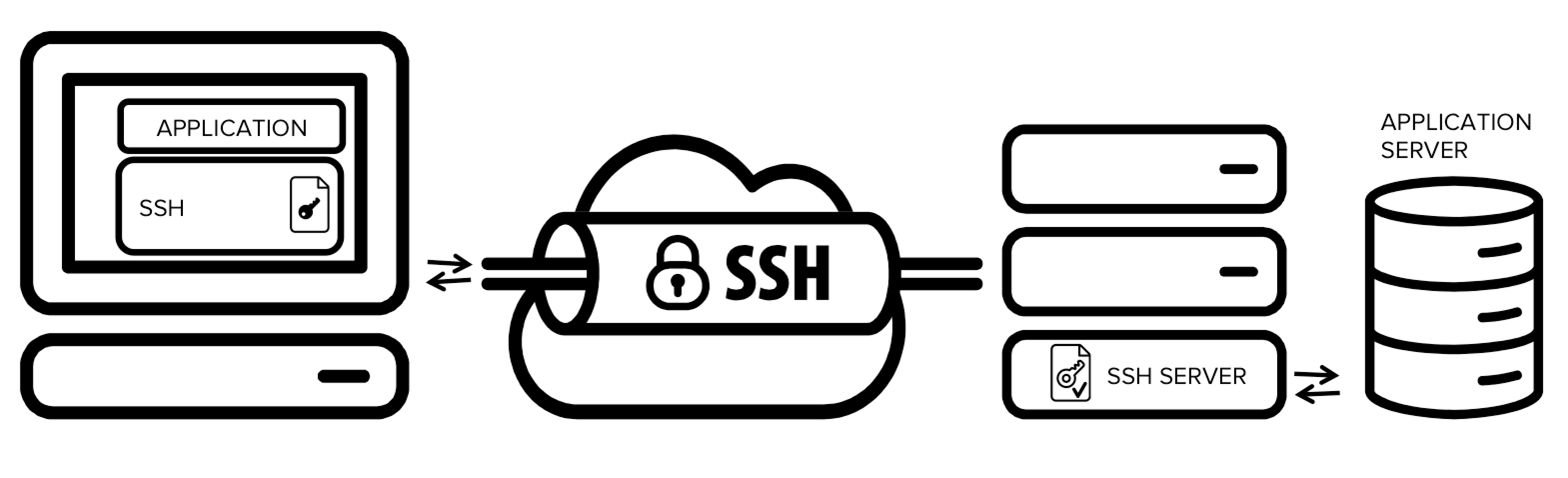
What Is An Ssh Tunnel Ssh Tunneling Learn the fundamentals of the ssh protocol, including key generation, remote shell access, and tunneling (sometimes called port forwarding); perform a adversary in the middle (aitm) attack in a simulated setting to demonstrate the security vulnerabilities of the telnet protocol;. Combined with attacks based on unmanaged ssh keys, ssh tunneling allows an attacker to utilize stolen ssh keys for an intranet from the public internet. ssh tunneling attacks can also be used for hiding the source of the attack. it is common or hackers to bounce attacks off systems and devices that allow ssh port forwarding to hide their tracks. There are several techniques to make your tunneling much easier, for quick use like in a ctf i think crafting the full ssh command is better and faster. for frequent connection, using sshuttle combined with a good ssh config can make your life much easier. In a tunneling protocol, packets are automatically encrypted. how to evade school firewall, secure traffic tunneling & more: client connects to server over tcp. client and server exchange available cryptographic primitives. client and server decide on a shared session key. the client sends the server their password.
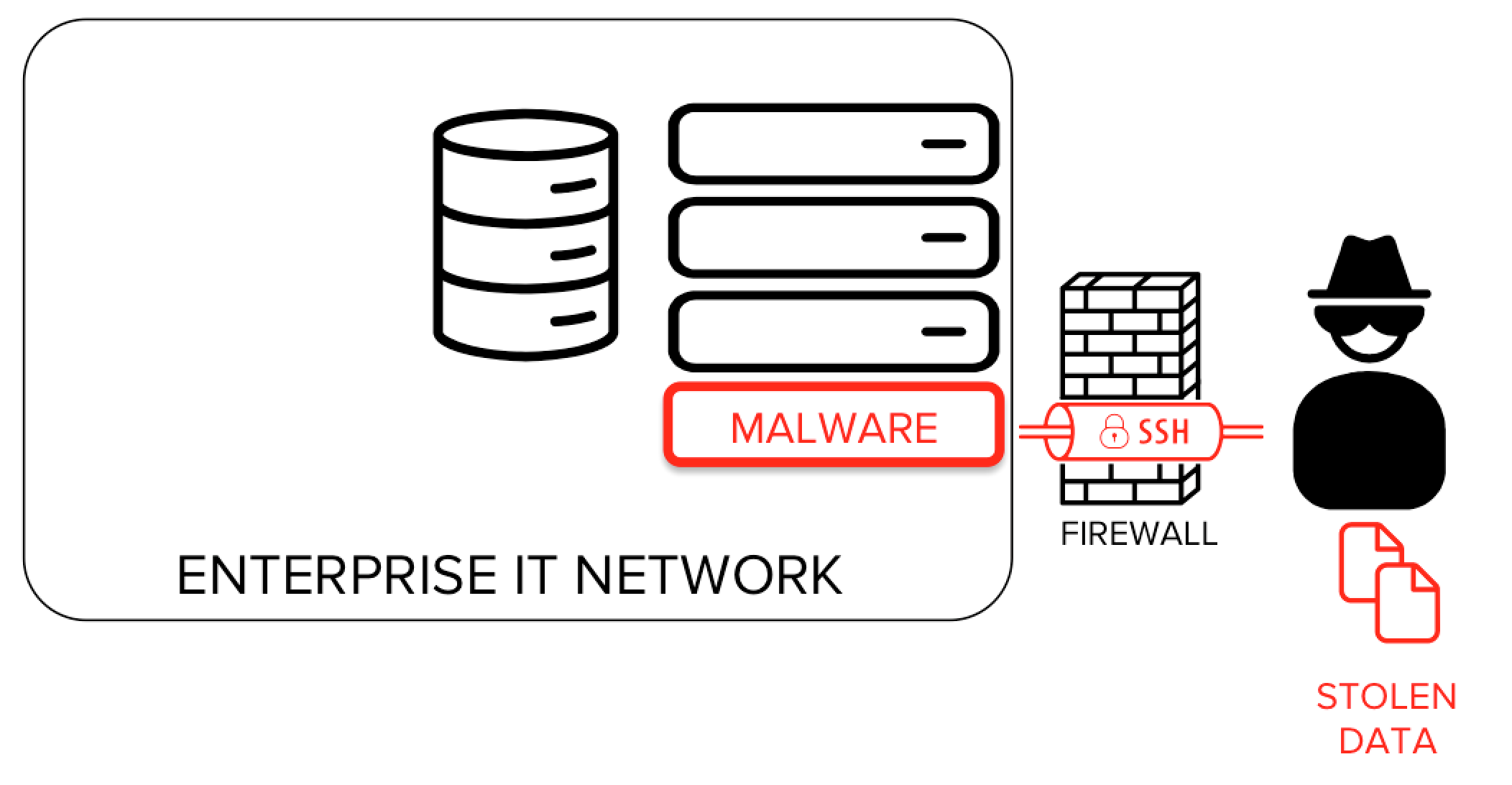
What Is An Ssh Tunnel Ssh Tunneling There are several techniques to make your tunneling much easier, for quick use like in a ctf i think crafting the full ssh command is better and faster. for frequent connection, using sshuttle combined with a good ssh config can make your life much easier. In a tunneling protocol, packets are automatically encrypted. how to evade school firewall, secure traffic tunneling & more: client connects to server over tcp. client and server exchange available cryptographic primitives. client and server decide on a shared session key. the client sends the server their password. There are three types of ssh port forwarding: local port forwarding. forwards a connection from the client host to the ssh server host and then to the destination host port. remote port forwarding. forwards a port from the server host to the client host and then to the destination host port. dynamic port forwarding. Ssh tunnels are a well known measure to securely forward connections to a remote machine. in most cases, ssh is fast, easy to setup, and easy to use, but it’s not without it’s drawbacks. learn what they are in this blog. Port forwarding 2020 ssh tunneling summary 12 10. 2018 2024 | cc by nc 4.0 | cc by nc 4.0. Ssh tunneling is a method used to establish a secure connection between two devices by encapsulating the data transferred within a secure ssh connection. this ensures that any sensitive information is encrypted and cannot be intercepted by third parties.

Ssh Tunneling Summary 300 Watts There are three types of ssh port forwarding: local port forwarding. forwards a connection from the client host to the ssh server host and then to the destination host port. remote port forwarding. forwards a port from the server host to the client host and then to the destination host port. dynamic port forwarding. Ssh tunnels are a well known measure to securely forward connections to a remote machine. in most cases, ssh is fast, easy to setup, and easy to use, but it’s not without it’s drawbacks. learn what they are in this blog. Port forwarding 2020 ssh tunneling summary 12 10. 2018 2024 | cc by nc 4.0 | cc by nc 4.0. Ssh tunneling is a method used to establish a secure connection between two devices by encapsulating the data transferred within a secure ssh connection. this ensures that any sensitive information is encrypted and cannot be intercepted by third parties.

Ssh Tunneling Summary 300 Watts Port forwarding 2020 ssh tunneling summary 12 10. 2018 2024 | cc by nc 4.0 | cc by nc 4.0. Ssh tunneling is a method used to establish a secure connection between two devices by encapsulating the data transferred within a secure ssh connection. this ensures that any sensitive information is encrypted and cannot be intercepted by third parties.

Comments are closed.