The Cia Triad 3 Security Pillars Confidentiality Integrity And Availability
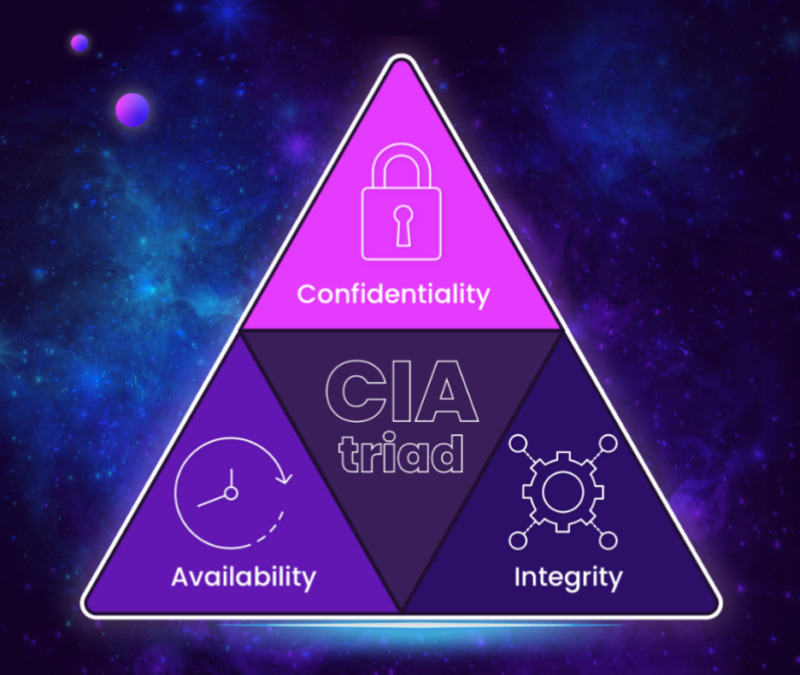
What Is The Cia Triad Why Is It Critical In Cybersecurity The cia triad refers to confidentiality, integrity and availability, describing a model designed to guide policies for information security (infosec) within an organization. the model is sometimes referred to as the aic triad which stands for availability, integrity and confidentiality to avoid confusion with the central intelligence agency. The cia triad—confidentiality, integrity, and availability—is a guiding model in information security. a comprehensive information security strategy includes policies and security controls that minimize threats to these three crucial components.

The Cia Triad Confidentiality Integrity Availability Panmore Institute The cia (confidentiality, integrity, availability) triad is a widely used information security model that can guide an organization’s efforts and policies aimed at keeping its data secure. Confidentiality, integrity, and availability or the cia triad is the most fundamental concept in cyber security. it serves as guiding principles or goals for information security for organizations and individuals to keep information safe from prying eyes. The cia triad is an information security model that is based on three pillars—confidentiality, integrity, and availability. this model provides organizations with a guide for establishing security procedures and policies that address these three critical areas. Our guide explores the three pillars of the cia triad, explaining their importance in protecting sensitive data and ensuring the overall security of information systems. learn about the various security controls and best practices that can help you achieve and maintain the desired levels of confidentiality, integrity, and availability for your.

Cia Confidentiality Integrity And Availability Triad Download The cia triad is an information security model that is based on three pillars—confidentiality, integrity, and availability. this model provides organizations with a guide for establishing security procedures and policies that address these three critical areas. Our guide explores the three pillars of the cia triad, explaining their importance in protecting sensitive data and ensuring the overall security of information systems. learn about the various security controls and best practices that can help you achieve and maintain the desired levels of confidentiality, integrity, and availability for your. The cia triad refers to the three core pillars of information security – confidentiality, integrity, and availability. these principles guide organizations and individuals in keeping information safe from unauthorized access or modification. The cia triad, consisting of confidentiality, integrity, and availability, serves as a foundational model for developing cybersecurity policies across various organizations. confidentiality focuses on restricting unauthorized access to sensitive information, ensuring that only authorized individuals can view or manipulate data. By integrating confidentiality, integrity, and availability into your security strategy, you can create a more resilient foundation for protecting data. these three elements help companies not only to comply with regulatory standards but also to strengthen trust with clients, partners, and stakeholders.

Three Pillars Cia Confidentiality Integrity Availability Stock Vector The cia triad refers to the three core pillars of information security – confidentiality, integrity, and availability. these principles guide organizations and individuals in keeping information safe from unauthorized access or modification. The cia triad, consisting of confidentiality, integrity, and availability, serves as a foundational model for developing cybersecurity policies across various organizations. confidentiality focuses on restricting unauthorized access to sensitive information, ensuring that only authorized individuals can view or manipulate data. By integrating confidentiality, integrity, and availability into your security strategy, you can create a more resilient foundation for protecting data. these three elements help companies not only to comply with regulatory standards but also to strengthen trust with clients, partners, and stakeholders.

What Is The Cia Security Triad Confidentiality Integrity By integrating confidentiality, integrity, and availability into your security strategy, you can create a more resilient foundation for protecting data. these three elements help companies not only to comply with regulatory standards but also to strengthen trust with clients, partners, and stakeholders.

Comments are closed.