What Is Zero Trust Network Access Ztna The Zero Trust Model Framework And Technologies Explained

What Is Zero Trust Network Access (ZTNA)? The Zero Trust Model ...
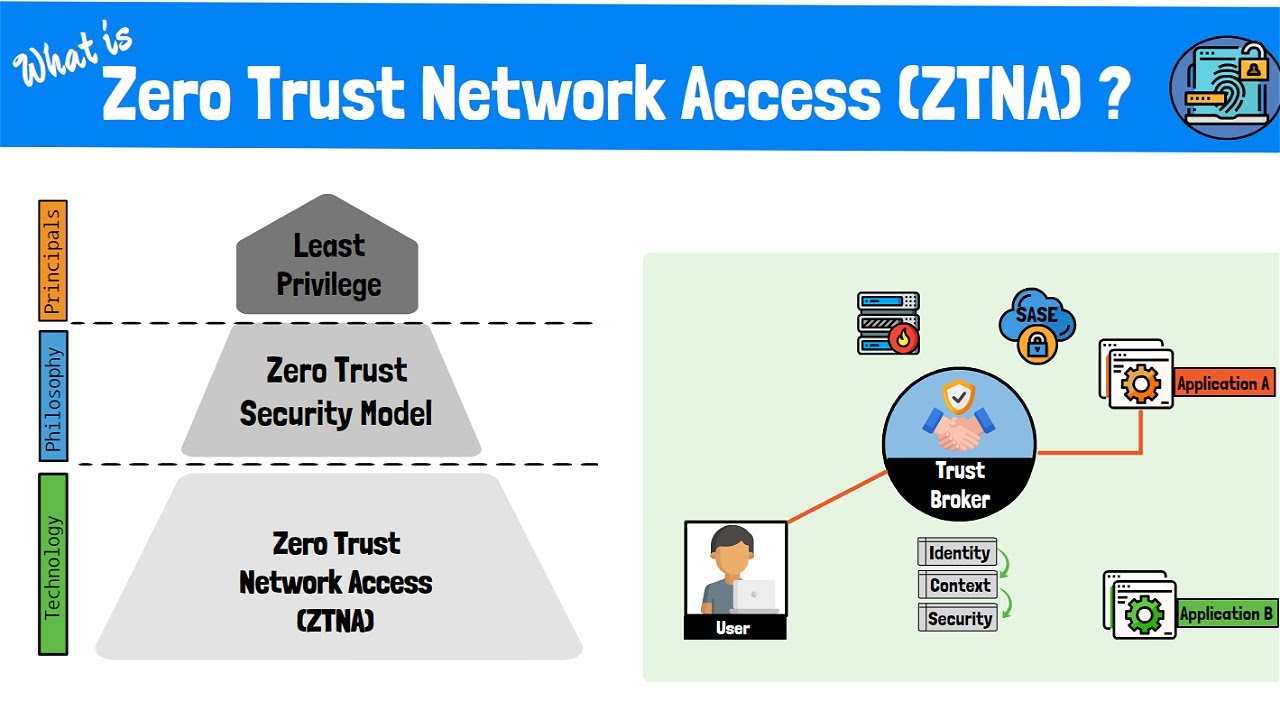
What Is Zero Trust Network Access (ZTNA)? The Zero Trust Model ... Zero trust network access (ztna) is a security model that provides secure, adaptive, and segmented access to applications and resources. it’s based on the principle of verify explicitly, use least privilege, and assume breach. Zero trust network access (ztna) is a security service that verifies users and grants access to specific applications based on identity and context policies. ztna removes implicit trust to restrict network movement and reduce attack surfaces. learn more about how a zero trust solution will secure your applications, networks, and data.

Types Of Zero Trust Network Access ZTNA Models Zero Trust Security ...
Types Of Zero Trust Network Access ZTNA Models Zero Trust Security ... This article explores zero trust network access (ztna), explaining its principles, architecture, benefits, and implementation steps. understand how ztna addresses modern security needs for businesses. Ztna is a category of technologies that offer secure remote access to applications and services on a per application basis, automatically setting up and tearing down tunnels as necessary. however, to understand ztna, it’s essential to know the model and frameworks it’s based on. Zero trust network access (ztna) is a set of technologies that enable secure remote access to internal applications. trust is never granted implicitly, and access is granted on a need to know, least privileged basis defined by granular policies. Ztna stands for zero trust network access and is, by definition, a security framework that strictly controls access to applications and data. unlike traditional security models that inherently trust internal networks, ztna follows the principle of ‘never trust, always verify’.

What Is Zero Trust Network Access Ztna The Zero Trust Model – Themeroute
What Is Zero Trust Network Access Ztna The Zero Trust Model – Themeroute Zero trust network access (ztna) is a set of technologies that enable secure remote access to internal applications. trust is never granted implicitly, and access is granted on a need to know, least privileged basis defined by granular policies. Ztna stands for zero trust network access and is, by definition, a security framework that strictly controls access to applications and data. unlike traditional security models that inherently trust internal networks, ztna follows the principle of ‘never trust, always verify’. Ztna uses an entirely different approach than traditional network security solutions, emphasizing secure remote access to corporate applications. this approach uses a granular user to application access control system rather than relying on a network security perimeter. In simple terms, ztna is a cybersecurity approach that assumes no user or device should be trusted by default — even if it’s inside the network. instead, it verifies identity and context every time a user connects to an application or resource. this approach lets businesses enable remote work and cloud operations securely. Zero trust network access (ztna) is a modern cybersecurity approach built on the principle of “never trust, always verify.” rather than assuming trust based on location or network boundaries, ztna enforces identity, context, and policy before granting access to any application or resource. Sometimes referred to as a software defined perimeter (sdp), ztna is an adaptive model wherein access to applications and services is granted on a least privileged basis as dictated by the organization’s access control policies.

What Is Zero Trust Network Access (ZTNA)_ The Zero Trust Model ...
What Is Zero Trust Network Access (ZTNA)_ The Zero Trust Model ... Ztna uses an entirely different approach than traditional network security solutions, emphasizing secure remote access to corporate applications. this approach uses a granular user to application access control system rather than relying on a network security perimeter. In simple terms, ztna is a cybersecurity approach that assumes no user or device should be trusted by default — even if it’s inside the network. instead, it verifies identity and context every time a user connects to an application or resource. this approach lets businesses enable remote work and cloud operations securely. Zero trust network access (ztna) is a modern cybersecurity approach built on the principle of “never trust, always verify.” rather than assuming trust based on location or network boundaries, ztna enforces identity, context, and policy before granting access to any application or resource. Sometimes referred to as a software defined perimeter (sdp), ztna is an adaptive model wherein access to applications and services is granted on a least privileged basis as dictated by the organization’s access control policies.

ZTNA Working Of Zero Trust Network Access Model PPT Template
ZTNA Working Of Zero Trust Network Access Model PPT Template Zero trust network access (ztna) is a modern cybersecurity approach built on the principle of “never trust, always verify.” rather than assuming trust based on location or network boundaries, ztna enforces identity, context, and policy before granting access to any application or resource. Sometimes referred to as a software defined perimeter (sdp), ztna is an adaptive model wherein access to applications and services is granted on a least privileged basis as dictated by the organization’s access control policies.
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
Related image with what is zero trust network access ztna the zero trust model framework and technologies explained
Related image with what is zero trust network access ztna the zero trust model framework and technologies explained
About "What Is Zero Trust Network Access Ztna The Zero Trust Model Framework And Technologies Explained"

















Comments are closed.